While information and also technology acquire more complex by the second, the necessity for database management is better than ever before since highlighted through the growth of various kinds of database management software in the market. Business owners and also brains of corporations know very well to invest a large section of their particular finances within a database management system which sets up just about all pertinent files within an efficient manner.
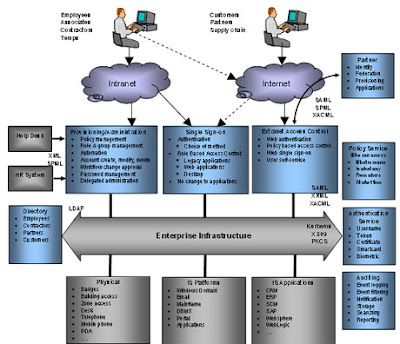
Database management plays an important role in many of market sectors and job areas, one example which is identification and access management. From the CIA right down to the closest 7-11, hypersensitive info is often obtained and also saved, whether it's a " inside info " authorities plan or bank card amount of a client. Vulnerable info could possibly be exposed to unauthorized entry in case a poor home alarm system is location because of the unproductive database management system. However, in the event that information is been able so wherein access is restricted depending on the identity from the person, secrecy of knowledge is just not jeopardized.
Database management can be crucial within relational database management. Information can just be stored with regard to taking uses, but most of that time period, it can be accessed to complete a number of deals and also routines. Through these instances, interactions involving different kinds of data have to be obviously described just before any kind of procedure takes place. By way of example, a few activities possess the right after structure: "if information Any and data B are genuine, next course of action Any happens; otherwise, procedure B can be accomplished." When associations among different kinds of data are certainly not effectively set up in advance, it's not hard to find out how techniques regarding these may go drastically wrong. It is essential that information is not only located correctly, but you are related to each other in the significant manner.
Because of the need for database management, nothing less than a talented database manager must preside more than managing databases. Publication rack willing to spend expensive for individuals designed with the essential expertise and knowledge. Those that have a strong basis in IT, computer science, and software design will discover a fulfilling profession in the field of database management. A formal qualifications in database management, whether obtained through knowledge as well as research, will really improve someone's benefit within the employment market.