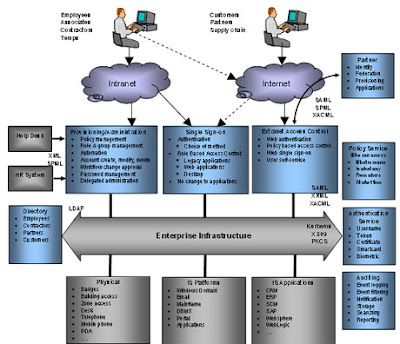
Every business features specific details which needs to be resistant to unauthorized customers. Identity Access management (IAM) is the method that enables business administration to identify along with handle information and also system resources through unauthenticated people. The main aim involving IAM is always to grant as well as reject the accessibility involving discreet information for the venture assets.
By using access management method, your approved government from the business organization can simply research along with identify the individual that can be accessing the trick info without having approval. For that reason, it can help business organization to meet their safety needs. Usually, Identity Access management comprises of segments like Validation, Authorization, Person Management and Key Individual Repository.
Certification entails affirmation regarding user Identity and pass word thereby delivering accessibility control along with personal privacy for the individual and the details with the firm. It will help in tracking the user's action over distinct sessions regarding connection involving the consumer and the computer system. On the other hand, Agreement verifies your approved person, no matter whether he/she has the approval to gain access to the individual data you aren't. That determines the access request up against the guidelines manufactured by the business. Acceptance involves checking regarding information such as individual qualities, person teams, channels and data resources that could be used and more.
The user management method in Identity Access management establishes specific features including security password resetting, identity design, tyranny of data etc. Apart from benefiting from this particular component, business organization also can choose implementing your Main Consumer Archive module for identity management. Central User Repository can retailer and also exchange id details from a single origin to numerous authorized sectors from the firm. That identifies the eye-sight of present identities as well as their relationship while using a variety of methods.
Now-a-days, numerous business owners make use of access management software to keep up privacy inside organization. By employing this software, business owners is able to reduce the price needed in employing human resources, as being a defender of the hypersensitive information. In addition to, additionally, it stops seepage of the secret choice created by the companies, which could be considered a a few concern when confronted with somebody rather than computer software.