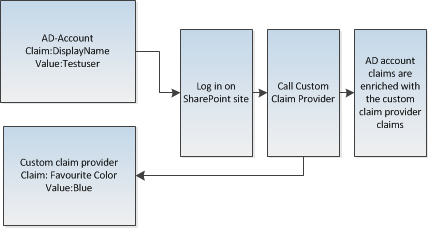
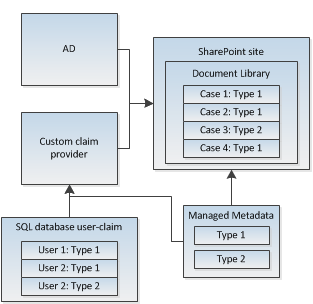
What I used for my project is ‘Claims Augmentation’ which means that for my authentication provider I still use AD accounts. These accounts however are enriched with user-specific claim information on the moment they log in on the SharePoint website. After that it is possible to base your security on the augmented claims.
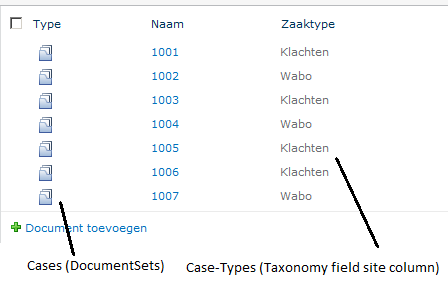
In my project ‘Case management’ plays an important role. I have created a Document Library and in that document library Document Sets are created of which each represents a different case. The most important aspect of these cases is that they are all of a certain type. Some users should have only access to cases of type 1, some users should only have access to cases of type 2 and some users should have access to both type 1 and 2. You get the picture
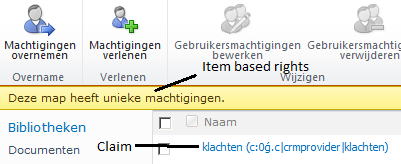
My solution is to use Item based security combined with claims based authentication. In my solution the claims are based on all possible case types. So for every case-type, there is a corresponding claim. On the moment of Document Set creation I break the role inheritance of the item (which is the Document Set), delete all other role assignments and add the role assignment of the claim that corresponds with the case-type. After that only users who possess the same Case-type claim have access to the Document Set and the underlying documents.
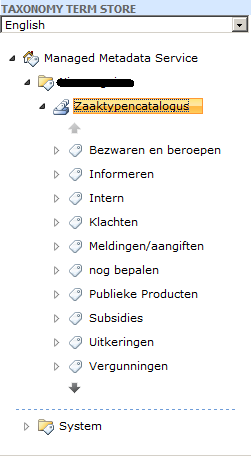
Remains the problem where I keep my list with all possible case-types (which is of course the same list that produces the claims). I decided to use Taxonomy feature of the Managed Metadata service for that. So now both the Case-type taxonomy metadatacolumn of my Document Set and the custom claims provider gets their list of claims/case-types from the Managed Metadata Service.
The custom claims provide uses a sql server table to determine which user has which claims. This table is queried each time a user logs in on the SharePoint website. It has a very simple structure with only 2 columns: username and claim.
The complete solution looks like this:
More Here
Courtesy:http://robertsep.wordpress.com/2011/01/16/claims-based-authentication-item-based-permissions-managed-metadata-solution/